Many critical infrastructures rely heavily on flow control for containment, control and movement, and the measurement of liquids, gasses, and slurries. Critical infrastructure providers (CIP) include water and wastewater, agricultural irrigation systems, oil and natural gas pipelines, discrete and process manufacturing, and transportation systems.
Operational technology (OT)[1], used in industrial control systems (ICS) for flow control, has been a critical part of operating, monitoring and maintaining physical infrastructure for decades. However, as OT has become digital, information technology (IT) has been an increasing part of that evolution, providing platforms, software and networks to enhance control and functionality.
Unlike IT, the core deliverable of OT is not information. Instead, the core deliverable of OT is a management of state. For example, if a valve needs to be opened or closed, OT can open or close it; If a gas pipeline experiences pressure beyond its operating parameters, OT can bring it back within tolerance levels.
The industrial internet stretches from traditional OT, such as supervisory control and data acquisition (SCADA) systems, to the emerging Internet of Things (IoT)[2] whose "nervous system" is digital and software-based. The Industrial Internet of Things’ (IIoT), sometimes referred to as Industry 4.0, control elements such as sensors, valve actuators and pumps are acquiring a "digital skin," exponentially increasing the digital presence in flow control ICS.
The nature of the risks is different between IT & OT worlds:
- Business risks are mainly related to the confidentiality and integrity of the data processed and hosted by the IT systems, which leads to intangible consequences such as loss of know-how and loss of reputation.
- For OT systems, business risks are related to the availability, integrity, reliability and safety of the ICS itself. Risks include operational consequences in the physical world such as production shutdown and financial losses, environmental damage and the inability to control the process or to obtain accurate information about its state.
Common beliefs that OT environments were impervious to outsider threats are now known to be false. Industrial corporations are increasingly connected with each other to improve efficiencies and OT systems are starting to resemble IT systems. To take advantage of the digital supply chain benefits, industrial corporations may allow suppliers to connect to automation systems for maintenance and asset management services. This integration provides significantly less isolation for OT from the outside world, creating a greater need to secure these systems. According to Frost & Sullivan,[3] the supply chain introduces weaknesses, allowing threats and entry point access to critical infrastructures which requires thinking of the value chain as a whole.
OT environments are vulnerable and exposed to cyberattacks. Persistent design vulnerabilities (PDVs) are inherent in OT systems as part of their function.[4] The International Society of Automation (ISA), describes it this way: "OT systems are not designed to ensure resilience against concerted attacks that intend to place components in dangerous operating states. This is expected to be a growing area of cyberattack and engineering research." As OT environments incorporate IT technologies, IT-related vulnerabilities are introduced.
Because of the longer OT life cycle (10 to 15 years), widely dispersed and legacy systems cannot be patched or upgraded in typical IT security fashion. As a result, OT environments remain highly vulnerable for long time periods.
Meanwhile, in addition to the nature of OT environments, the knowledge and skills needed to attack OT networks are spreading rapidly, so that the OT-related cyber risks have reached a critical threshold and require immediate action.
OT cybersecurity and regulatory risk
It is generally accepted that a significant governance, knowledge, and experience gap exists between the IT and OT domains. OT staff have process engineering expertise but little or no cybersecurity training and understanding. Closing this gap to make OT staff part of the cybersecurity chain is critical.
More broadly, on behalf of senior executives, chief security officers (CSO) and chief information security officers (CISO) are requested to establish a consistent cybersecurity operating model integrating the OT environments to address the following issues:
- What are the major OT assets to protect? Are they vulnerable? Where are they located? Are external and internal threats considered? Does the organization understand the origin of threats (e.g. cyber criminals, competitors, governments, rogue employees, etc.)?
- How shall OT cybersecurity be governed within the organization? Is it well-integrated into the corporate governance? Are the roles and accountabilities well-defined among industrial site directors, IT, OT and cybersecurity stakeholders?
- What are the major OT cyber risks the organization faces? What are the risks of compromising the OT network to enter the corporate IT network or vice versa? Is the organization able to detect abnormal events and weak signals of cyberattacks?
- How can OT staff members be made aware of their roles related to cybersecurity? Did control engineers receive some basic cybersecurity awareness training?
- In the event of a serious OT cyber incident, which incident response and crisis management process needs to be developed?
Especially for CIP or operators of essential services, increasing regulatory pressure will require the CSO and the CISO to accelerate the enforcement of cybersecurity best practices and the readiness to detect and provide notification of severe cyber incidents.
The United States National Institute of Science and Technology (NIST) Framework and the European Networking and Information System (NIS) Directive requires critical operators to conduct risk assessments exercises and to detect and provide notification of their severe cyber incidents to the national or federal information security agencies (to avoid potential systemic effects). Therefore, the main current CSO and CISO challenge is to raise awareness at the industrial director’s level and to increase their influence across the organization to address in a holistic way increasing OT-related risks.
Figure 2. The pillars of OT cybersecurity
The challenges of operational cybersecurity in OT environments
OT cybersecurity derives many practices and technologies from IT security. However, changing the state of a system has unique safety, business continuity and security implications. This means that merely translating IT security practices and copying IT security technology to address OT security will not result in a secure OT environment.
In IT environments, technology is already there and security operations centers (SOC) have been set up to monitor and detect cyberattacks although in many cases, IT cyber-compromised systems have gone undetected for months. In the OT world, the use of active cybersecurity solutions (e.g. firewalls, intrusion detection systems, antivirus, vulnerability scanners, etc.) has limited value for several reasons:
- For existing systems, implementing such security solutions is limited by the risks of false positive events, which might create perturbation on mission-critical OT networks.
- Such IT technologies are too intrusive for mission-critical and low-latency systems for which false positives are not acceptable.
- Most OT components in the field today such as PLC, controllers, remote terminal units (RTU), and intelligent electronic devices (IED), do not support any third-party IT security software.
The biggest challenge in OT environments remains to manage OT systems to reduce the attack surface and then to know when a cyberattack occurs or has already started and respond rapidly so that corporations can ensure business resilience of their industrial operations.
Consequently, a reasonable approach to protect an OT system is to implement active cybersecurity solutions where possible (meaning where it will not disturb the system) and passive monitoring solutions without taking the risk of disrupting the OT system by generating false positive events. Focus should be on monitoring solutions that are tailored to the unique characteristics of OT environments (i.e. mission-critical, low-latency and long life cycle).
The cyber control room
A cyber control room is a security operations center (SOC) dedicated to OT environments. It is simply defined as a virtual facility for monitoring cybersecurity of OT networks and assets. Through sensors that are the equivalent of cameras in the physical world, data can be collected from different OT environments.
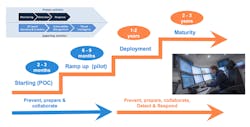
Figure 3. Implementation of a cyber control room
The greatest value in a cyber control room comes from its early and accurate detection capability as well as its ability to streamline collaboration between OT staff, IT staff and cybersecurity experts. Its ease of integration with an IT SOC by correlating IT and OT events enhances organizational detection capabilities as a whole.
Establishing a cyber control room is a must-have to win the OT cybersecurity battle, but it represents a long journey for industrial corporations, particularly to be able to continuously monitor all the OT components in a 24/7 mode. Such a cyber control room will entail positive side effects: deal with legacy OT equipment, empower OT operators and staff, etc. As shown in Figure 3, industrial corporations must adopt a step-by-step pragmatic approach to avoid making the process so complex that goals are never achieved.
References
[1] Gartner defines OT as "hardware and software that detects or causes a change of state, through the direct monitoring and/or control of physical devices, processes and events in the enterprise."
[2] The Internet of Things (IoT) is defined as "the network of physical objects that contains embedded technology to communicate and sense or interact with the object’s internal state or the external environment."
[3] Top Ten Cyber Trends Affecting the CNI Sector » (Frost & Sullivan 2014)
[4] The ISA refers to these not as "zero-day vulnerabilities" but as "infinite day vulnerabilities" because vulnerabilities are a combination of new and inherent vulnerabilities of the systems.
Ed Nugent
Laurent Hausermann
Ed Nugent is the chief operating officer (COO) of PcVue Inc. of Woburn, Massachusetts, the North American affiliate of ARC Informatique; the publisher of PcVue Solutions for SCADA, HMI and BMS. He has been active in development and implementation of SCADA and OT Solutions, with a focus on cybersecurity, for more than 35 years. Nugent can be reached at [email protected].
Laurent Hausermann is Sentryo‘s co-founder & COO. Laurent is passionate about software, hacking and innovation. He spent the last 15 years creating cybersecurity products to defend large and small organizations. Hausermann can be reached at [email protected].